Latest News And Updates
Thursday
13 Types of Infographics You Should Be Creating [Infographic]
Posted By: Arin Dey - October 27, 2022Monday
Drawbacks and limitations of Google Analytics 4
Posted By: Arin Dey - June 27, 2022- There is no simple way to migrate your data
- Not-so-intuitive user interface
- Limits on custom dimensions
- Lack of custom channel grouping
- Google may have been disappointed with the speed of adoption for Google Analytics 4 and decided to act decisively.
- Google circumventing some of the legal heat that Universal Analytics is facing in the EU.
- Google wanting to cut costs and rid itself of technical debt associated with thousands of websites with legacy solutions installed. Since GA4 is designed to support Google’s advertising network, it guarantees more revenue than the competition.
Tuesday
5 Digital Marketing Trends in 2022 [Infographic]
Posted By: Arin Dey - February 01, 2022Change is the law of life. And for anyone working in the digital marketing world, it’s very important to be aware of the ongoing and upcoming trends in order to stay ahead of their competition and thrive alongside future technologies and innovations.
Now that we’ve covered everything about the upcoming digital marketing trends of 2022 in following infographic..
Top 5 Cyber Security Concerns 2021 [Infographic]
Posted By: Arin Dey - August 31, 2021Sunday
What is Blockchain and how does it work?
Posted By: Arin Dey - February 28, 2021As a friend, you assess the situation and agree to send the amount requested. So, you reply, “Sending right away, Dave.”
You may call your bank and raise a request, “Please transfer $2,000 from my account to Dave’s account.”
Your account manager replies, “Yes, I will do that now.”
Your account manager opens your bank register, checks your account balance to see if you have enough balance to transfer $2,000 to Dave. You have plenty and, thus, he makes an entry in the register like the following:
February 28, 2021
#--------------- Transferred------------ $2,000------------- Dave
You may call Dave and tell him, “I’ve transferred the money. You may withdraw the amount $2,000 now from your bank.”
In this example, you and Dave both trusted the bank to manage and transfer your money. In this process, there was no hard copy of bills used to transfer the money, just an entry in a register. that neither you nor Dave controls or owns.
This is the “problem” of the current system: we depend on individual third-parties to establish trust between ourselves. But, you might say, we’ve been depending on middlemen to establish between different parties for ages. Why is it a problem?
The problem here is that they are one, and only one, authority here. Anytime that single point of contact may go corrupt without your knowledge. Imagine these situations:
The register in which the transaction was logged becomes corrupted.
The bank mistakenly writes $4,000 on the register instead of $2,000.
So, with that in mind, let’s think out of the box now! Is there a way to maintain the register amongst ourselves instead of someone else doing it for us? Or, put another way, Is it possible to find a system where the transfer of money will happen without needing a bank? is the answer to this question. It is a method to maintain that register among ourselves instead of depending on a bank or another third party to do it for us.
Saturday
How To Write A Persuasive Email [Infographic]
Posted By: Arin Dey - January 30, 2021Source: Resume.io
Monday
Data Protection Concerns And How To Protect It
Posted By: Arin Dey - November 16, 2020In general terms, data protection concerns three areas:
- securing data, especially personal data such as bank account numbers, TANs and PINs, against theft and misuse;
- protecting data against viruses and other malware; and
- protecting data in case of a hardware failure.
So, data protection is more than just virus protection and passwords. But many users ignore the protection of their data. You probably know someone who has four or five broken cellphones at home. Of the data that used to be on those phones, what was saved on the SIM card may have been saved. It’s similar with laptops and tablets. Whenever a device fails, data is lost. It might just be letters and e-mails, but mostly it’s photos – and when they’re gone, beautiful memories are lost forever. But contracts and other documents can also be lost. Data losses are therefore both material and non-material.
The most important tips for protecting against spying on passwords – in other words, the basic rules for data protection – are:
- Never use the same password for multiple accounts.
- Never use words that are in a dictionary or that consist of numbers (birthdays or lottery numbers) as passwords, because these can easily be generated by a generator.
- Change your password regularly.
- Don’t keep a list of passwords on one of your computers or smartphones.
Advantages of backup solutions
The advantages of backup solutions are obvious.
- The data backup is carried out automatically so that the user cannot forget to back up his pictures, contacts, telephone numbers, emails, and documents.
- The backup runs in the background and doesn’t interfere with the computer, smartphone, or tablet as much as direct copying.
- With a cloud backup, secure storage systems are used in a data centre of the backup solution provider and the user doesn’t have to worry about the procurement and operation of the backup drives.
- Thanks to convenient setup wizards, users don’t have to learn how to operate additional software, but can concentrate on what’s important.
A backup is therefore more than just a copy of the data. But the backup must also be planned. Once planned, the data can be restored in almost any situation.
The three golden rules of data protection
Rule 1: An important prerequisite for data protection is the awareness of the correct handling of passwords, the appropriate selection of devices (from PCs to tablets to smartphones), and the correct selection of cloud services.
Rule 2: Assess what data you have, where it is currently stored, how important it is, and whether you have access to this data. Such an inventory will reveal vulnerabilities in data protection, from passwords stored in files to external hard drives that are no longer accessible.
Rule 3: Use backup software. Especially if you want to back up many different devices, backup software, including cloud storage, is recommended. You should also use this backup software to regularly test whether the data can be restored.
Source: B2C
Friday
A Primer on Edge Computing
Posted By: Arin Dey - August 28, 2020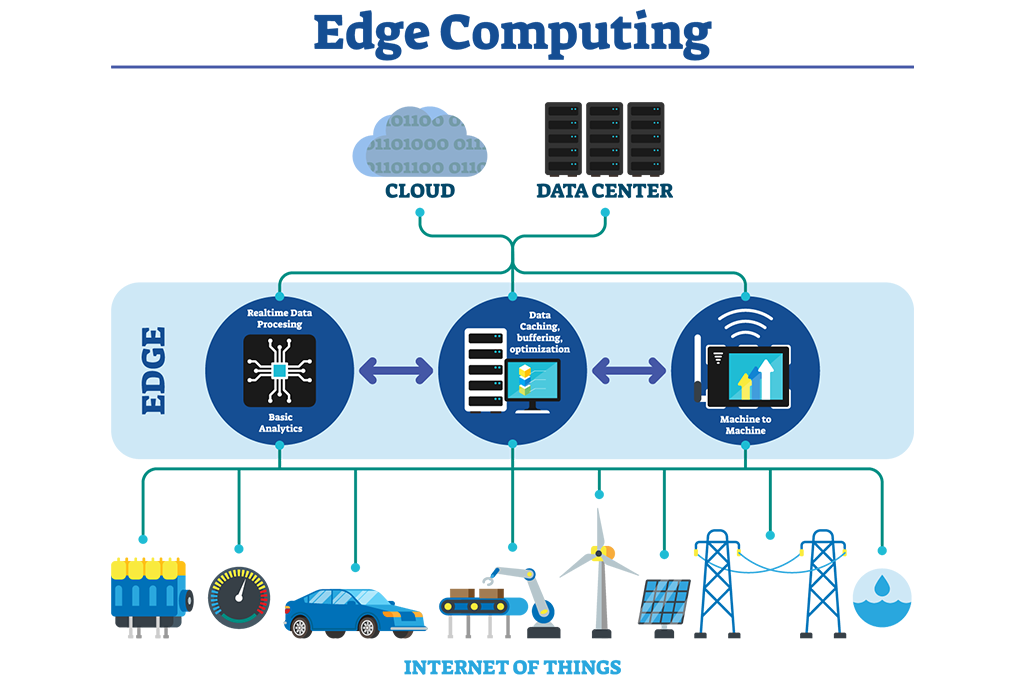
- Lesser Network Load
- Zero Latency
- Reduced Data Exposure
- Computational Efficient
- Costs and Autonomous Operation
- Security and Privacy
- Edge-to-Cloud data exchange capabilities
- Common-on-Edge data exchange capabilities
- Streaming Data Analytics and Batch frameworks and APIs
- Controlled rolling and Versioning upgrades of applications
- Status of application monitoring from an Ad-Hoc Cloud Dashboard
- Cloud-Based Deployments of Edge Computing Applications
- Edge-to-Cloud data exchange capabilities
- Common-on-Edge data exchange capabilities
- Streaming Data Analytics and Batch frameworks and APIs
- Controlled rolling and Versioning upgrades of applications
- Status of application monitoring from an Ad-Hoc Cloud Dashboard
- Cloud-Based Deployments of Edge Computing Applications
- New Functionalities are offered.
- Easier configurations.
- Hacking Potential is increased.
- The load on the server is reduced.
- Load on Network is reduced.
- Application Programming Interface.
- Increases Extensibility.
- Centralized Management.
- Costs of Licensing.
- Support and Updates.
- Speed is increased.
- Reliability is increased.
- The random issue is reduced.
- The compliance issue is reduced.
- Hacking issues are reduced.
- Random issues are reduced.
Tuesday
Tips to Success in Bisuness - Outsourcing Social Media [Infographic]
Posted By: Arin Dey - June 02, 2020




















![How To Write A Persuasive Email [Infographic] How To Write A Persuasive Email [Infographic]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhTtuZap_wDjP9n-diXFGKATdvwCuoce3WkEehHGMM8fKT0HgwZw3LwMftKUb1At8c-nbFNOcbzS_GasbGgWLyzfbCs1AItq9mkbfuRjhkwHhdgLuyfOtoGYQcEyd7K-7ag0uacQmfGcw5r/w640-h410/How-to-write-a-persuasive-email.png)


 Recent
Recent Tags
Tags Popular
Popular




